1. Overview of Cybersecurity Threats
Cybersecurity threats refer to malicious activities aimed at damaging, stealing, or disrupting digital systems, networks, and data. Understanding these threats is essential to implementing effective security measures that protect individuals and organizations.
2. Categories of Cybersecurity Threats
Cyber threats can be categorized based on their intent, techniques, and impact. Major categories include:
-
Malware Attacks
-
Phishing and Social Engineering
-
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
-
Man-in-the-Middle (MITM) Attacks
-
Zero-Day Exploits
-
Insider Threats
-
Advanced Persistent Threats (APTs)
2.1 Malware Attacks
Malware (malicious software) is designed to infiltrate and damage systems. Common types include:
-
Viruses: Attach to legitimate files and activate when executed.
-
Worms: Self-replicating malware that spreads across networks without user intervention.
-
Trojans: Masquerade as legitimate software to deceive users.
-
Ransomware: Encrypts data and demands payment for decryption.
-
Spyware: Secretly monitors user activity and collects sensitive data.
2.2 Phishing and Social Engineering
These attacks manipulate individuals into disclosing confidential information through deception:
-
Email Phishing: Fraudulent emails posing as trustworthy sources.
-
Spear Phishing: Targeted attacks on specific individuals or organizations.
-
Vishing (Voice Phishing): Scams conducted via phone calls.
-
Smishing (SMS Phishing): Fraudulent text messages designed to steal credentials.
2.3 Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
These attacks flood systems with excessive traffic to disrupt normal operations:
-
Application Layer Attacks: Target web apps with requests to exhaust resources.
-
Volumetric Attacks: Saturate bandwidth, making networks inaccessible.
-
Protocol Attacks: Exploit flaws in network protocols to exhaust server resources.
2.4 Man-in-the-Middle (MITM) Attacks
Attackers intercept and manipulate communications between two parties:
-
Session Hijacking: Gaining control of a valid user session.
-
Eavesdropping: Secretly monitoring private communications.
-
SSL Stripping: Downgrading HTTPS connections to unencrypted HTTP.
2.5 Zero-Day Exploits
These target software vulnerabilities unknown to the vendor:
-
Zero-Day Malware: Exploits a flaw before a fix is available.
-
Targeted Zero-Day Attacks: Aimed at high-value infrastructure or organizations.
2.6 Insider Threats
Threats originating from within the organization, often involving trusted personnel:
-
Insider Misuse: Employees exploiting access for sabotage or personal gain.
-
Unintentional Insider Threats: Mistakes or negligence leading to security breaches.
-
Malicious Insider Attacks: Deliberate theft or exposure of sensitive data.
2.7 Advanced Persistent Threats (APTs)
Long-term, highly targeted cyberattacks by skilled adversaries:
-
Long-Term Infiltration: Attackers remain hidden within networks for extended periods.
-
Sophisticated Methods: Use of custom malware, phishing, and zero-day exploits.
-
Strategic Targets: Typically aim at governments, defense sectors, or large enterprises.
3. Conclusion
A comprehensive understanding of cybersecurity threats enables individuals and organizations to prepare and respond effectively. Recognizing these categories is the first step toward building a robust defense. Future lessons will explore countermeasures, detection tools, and cybersecurity frameworks to enhance resilience.
Lesson 4
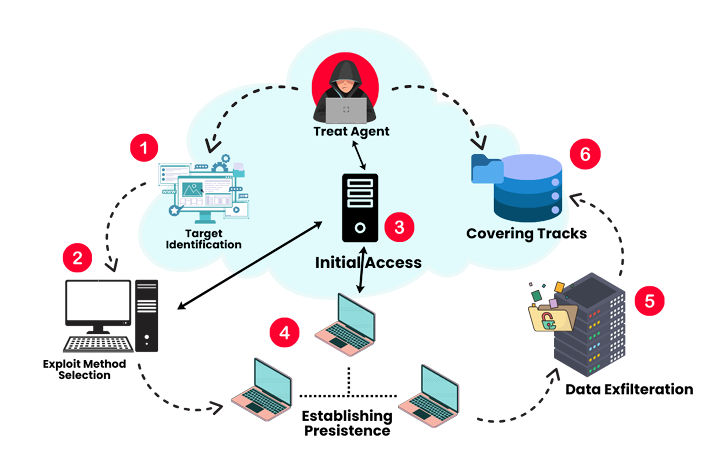
1. Overview of the Cyber Kill Chain
The Cyber Kill Chain is a cybersecurity framework developed by Lockheed Martin that outlines the stages of a cyberattack. It is used to help organizations understand attacker behaviors, detect malicious activity early, and implement defensive strategies to prevent breaches.
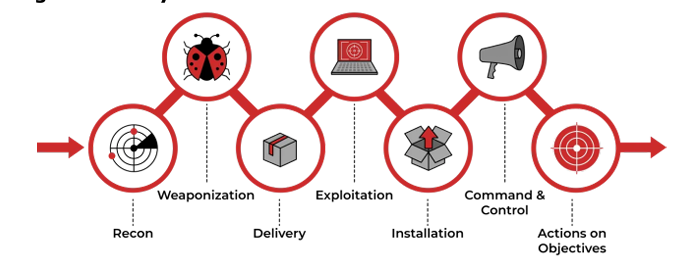
2. Stages of the Cyber Kill Chain
The model breaks down a cyberattack into seven stages, each representing a critical step in the attack lifecycle:
1. Reconnaissance
-
Description: The attacker gathers information about the target.
-
Methods:
-
Open-source intelligence (OSINT)
-
Social engineering
-
Network scanning
-
-
Defenses:
-
Security awareness training
-
Threat intelligence monitoring
-
Minimizing publicly available information
-
2. Weaponization
-
Description: Creation of a malicious payload using exploits or malware.
-
Note: No contact with the target at this phase.
-
Defenses:
-
Secure software development practices
-
Malware sandboxing
-
Threat intelligence analysis
-
3. Delivery
-
Description: The attacker sends the weaponized payload to the target.
-
Common Methods:
-
Phishing emails
-
Malicious websites
-
Infected USB drives
-
-
Defenses:
-
Email filtering
-
Web security gateways
-
User awareness training
-
4. Exploitation
-
Description: The attacker exploits a system vulnerability to trigger the payload.
-
Examples:
-
Software flaws
-
Social engineering
-
Misconfigurations
-
-
Defenses:
-
Regular patching and updates
-
Endpoint protection solutions
-
Proper access control policies
-
5. Installation
-
Description: Malware is installed to establish persistence.
-
Goal: Maintain access to the system over time.
-
Defenses:
-
Application whitelisting
-
Intrusion Detection Systems (IDS)
-
Endpoint Detection and Response (EDR)
-
6. Command and Control (C2)
-
Description: The attacker sets up a communication channel with the compromised system.
-
Purpose:
-
Remote control
-
Data exfiltration
-
Launching additional attacks
-
-
Defenses:
-
Network traffic monitoring
-
Strict firewall configurations
-
Anomaly and behavior-based detection
-
7. Actions on Objectives
-
Description: The attacker achieves their intended goal.
-
Examples:
-
Data theft
-
Espionage
-
Ransomware deployment
-
System destruction
-
-
Defenses:
-
Strong incident response plans
-
Data encryption
-
Continuous security monitoring
-
3. Importance of the Cyber Kill Chain
-
Early Threat Detection: Allows identification and disruption of attacks before damage occurs.
-
Informed Defense Strategy: Enables tailored security controls at each attack stage.
-
Structured Incident Response: Provides a roadmap for responding to cyber incidents.
-
Enhanced Threat Intelligence: Helps organizations analyze and respond to adversary tactics.
4. Adapting the Cyber Kill Chain for Modern Threats
While valuable, the Cyber Kill Chain has limitations with modern attacks (e.g., insider threats, supply chain attacks). Enhancing the model with additional frameworks improves overall defense:
-
MITRE ATT&CK: A detailed matrix of adversary tactics, techniques, and procedures (TTPs).
-
Defense-in-Depth: Implements layered security controls across the network.
-
Zero Trust Architecture: Assumes no implicit trust, verifying all users and devices continuously.
Conclusion
The Cyber Kill Chain remains a foundational tool for understanding and disrupting cyberattacks. By integrating it with modern security frameworks and strategies, organizations can significantly improve their ability to detect, respond, and recover from cyber threats.
TryHackMe Practice Room: Cyber Kill Chain – TryHackMe
🔗 PDF Links:
🔗 Video Link:


Comments
Post a Comment